Mastering MetaMask: Understanding Account Hierarchies and Security Issues

MetaMask is a widely-used crypto wallet software that facilitates interaction with the Blockchain and the execution of crypto transactions. Although its user interface is friendly, the underlying complexities can make it difficult to understand. MetaMask poses numerous security issues that require the attention of its users.
This article aims to help users of hot wallets like MetaMask understand its core components and the process by which these components are generated. Starting with these fundamentals, users can better grasp the security precautions needed to protect their digital assets.
Components in MetaMask
MetaMask password and seed phrase
When installing the MetaMask plugin on a browser for the first time, users are prompted to create a password and select a 12-word seed phrase. This phrase is also known as a mnemonic phrase or a Secret Recovery Phrase (SRP). The seed phrase is randomly generated using a specific cryptographic algorithm. The high degree of randomness, or entropy, in the seed phrase generation, ensures the critical information cannot be guessed or reproduced.
Once the MetaMask extension is installed on a browser and a seed phrase is configured, the MetaMask account is linked to the browser until it's uninstalled.
The roles of the password and seed phrase are as follows:
MetaMask Password: The password is used to unlock the extension in a specific browser and decrypt locally stored data. It has no direct relation to the wallet accounts themselves.
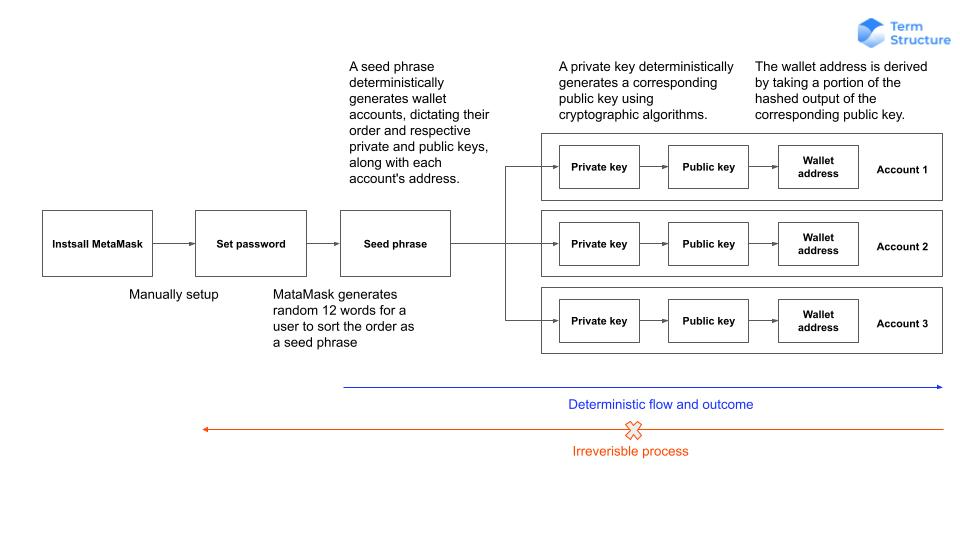
Seed Phrase: A seed phrase deterministically generates wallet accounts, dictating their order and respective private and public keys, along with each account's address.
Wallet account, private key, and public key
The seed phrase can be used to generate the associated wallet accounts. Each wallet account contains three essential components: the private key, the public key, and wallet address.
Unlike the seed phrase that is generated randomly, the creation of the wallet account follows a deterministic process. This implies that all wallet addresses and keys, derived from the same seed phrase, will remain identical regardless of the number of times they are regenerated.
The functionality of the three components is shown below.
Private key: This is essentially a secret password that a user should never share with anyone. It's used to sign transactions, meaning it provides mathematical proof that they have come from the owner of the wallet. Each private key in the wallet is generated from the seed phrase with a specific cryptography algorithm.
Public key: This is derived from the private key. The public key can be freely shared and is used by others to encrypt messages to you or verify messages from you.
Wallet address: This is derived by taking a portion of the hashed output of the corresponding public key. The wallet address represents a user’s account on the blockchain. It's like an email address - you can share it with others so they can send you cryptocurrency.
The generation sequence for the seed phrase, private key, public key, and wallet address is predefined and inflexible. This process is irreversible, meaning that it is not feasible to derive the private key or seed phrase from the wallet address or public key.
The structure of MetaMask components and their generative logic is displayed as follows:
Security in MetaMask
Security in different components
The MetaMask structure may be categorized into two levels:
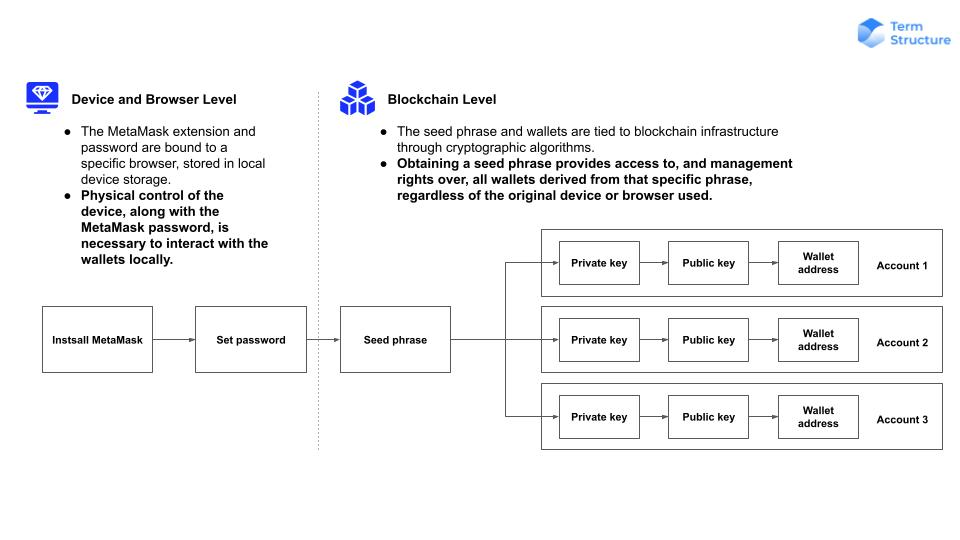
Device and Browser Level
The MetaMask extension and the password you set are bound to a browser on a device. They are the mechanism to protect user data on local storage devices and the interface that allows users to interact with the Blockchain. But the security at this level is not directly related to the Blockchain.
The password is used to unlock the extension on a particular browser and decrypt the locally stored data. The generation of seed phrase has nothing to do with the password. Therefore the password alone does not grant access to the seed phrase or private keys.
However, if someone gains access to the device and the browser where MetaMask is installed, and they have your password, they could potentially interact with your wallets, make transactions, or even reveal the seed phrase from within the extension.
Blockchain level
The seed phrase is used to deterministically generate associated wallets, which include their respective private keys. The seed phrase, by itself, grants access to the private keys and consequently, to all assets within the wallets.
A single private key within a wallet is utilized for signing transactions. In case a private key is compromised, the corresponding wallet's assets could be entirely appropriated. Even if only one private key is compromised, other wallets under the same MetaMask account could still be at risk, especially if the leak resulted from malware or a phishing attack.
Device & Browser level vs. Blockchain level
The main difference between device and browser level and Blockchain level are:
- At the device and browser level, a hacker would need to gain access to the entire device and know the MetaMask password to steal assets from all associated wallets.
- At the blockchain level, if the seed phrase is compromised, anyone can use it to recreate the wallets and steal all associated assets, regardless of device or password security.
- If a single wallet's private key is leaked, it can be imported into another MetaMask wallet, regardless of its seed phrase or password. This bypasses the need for device and password compromise as well as the need for the original seed phrase.
The following chart shows the concept of security in different components of MetaMask:
Levels of Severity in Various Types of Security Breaches
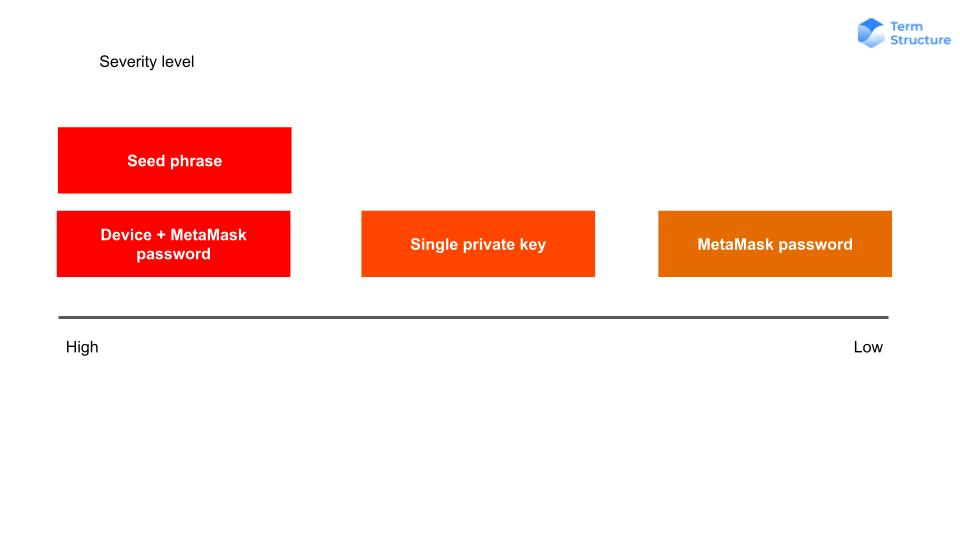
The severity of a security breach can differ significantly based on the type of compromise:
- Immediate Risk to All Wallets in a MetaMask Account:
If a seed phrase is revealed or if a device, along with the MetaMask password, is compromised, all assets in all wallets under the MetaMask account are immediately at risk. There is a high likelihood that the hacker may transfer all the assets.
- Immediate Risk to a Single Wallet:
If a single private key is exposed, the assets in that particular wallet are immediately at risk. Although the assets in other wallets remain safe, it's strongly recommended to transfer the assets from the compromised MetaMask account to a new one as soon as possible. This is because the exposure of a key might suggest that your device has been compromised.
- Potential Risk to Assets:
If the MetaMask password is compromised but the device remains secure, the assets are not immediately endangered. However, it is highly recommended to transfer your assets to a new MetaMask account promptly to prevent potential losses.
The following highlights the severity levels associated with different types of compromise incidents:
Conclusion
MetaMask wallet users must prioritize their understanding of MetaMask operations, wallet security, and the inherent sensitivity of data leaks. MetaMask, as a browser-based wallet, provides an accessible and user-friendly gateway into the world of cryptocurrencies. However, its ease of use should not overshadow the importance of stringent security measures.
It is crucial to understand the architecture of MetaMask, including seed phrases, private-public key pairs, and associated wallet accounts. It ensures users are aware of the potential risks and safeguards associated with their transactions. A seed phrase, for instance, holds the keys to all associated wallet accounts. A leak of this phrase could lead to devastating asset loss.

